As the number and size of cyber attacks on businesses continues to increase, the risk of experiencing a data breach is higher than ever. The resulting cost of these breaches can be significant – according to thePonemon Institute’s 2017 Cost of Data Breach Study, these totalled $2.51 million per year across the organisations that were recruited for the research.
As a result, an increasing number of organisations are choosing to invest in a cyber insurance policy, which allows them to claim cyber incident response expenses, regulatory fines, legal defence costs and business interruption losses. In other words, offset the cost of a potential data breach.
This article outlines the benefits of cyber insurance and explains why, in today’s digital age, it is vital for organisations to invest in this class of insurance, in addition to understanding the information governance obligations that their insurance policy places on them.
What is a cyber incident?
A cyber incident refers any event that threatens the security, confidentiality, integrity, or availability of information assets (electronic or paper), information systems, and/or the networks that deliver the information. Any violation of computer security policies, acceptable use policies, or standard computer security practices is classified as a cyber incident. (Source : CABQ)
Information governance, along with risk management, may not prevent a cyber attack from occurring, but it can certainly reduce its impact on the affected company. A cyber threat or breach leaves the company exposed to a loss of integrity and compromised access to information. This also results in the inability to provide the right information to stakeholders and the failure to respond to regulatory obligations. Mature cyber risk governance and risk management plans can prevent the disruption of information governance.
Transfer of risk
When dealing with questions of risk transfer, executives may choose to self-insure. According to the Ponemon Institute’s 2017 Cost of Data Breach Study,, the average per cost per capita (per compromised record) of a data breach was $139 per organisation surveyed, with the average cost of data breach totalling $2.51 million. Thus a business experiencing at least two data breaches a year could be expected to set aside $5 million of company funds for data breach response. In such a scenario, investors are likely to find shareholder returns diminish over time compounded with reputational loss.
Investing in cyber insurance not only frees up investors’ resources, it is also more cost effective in the long term. In transferring risk to the insurer, businesses must give proof of their information governance practices. If there are no practices in place, the insurance can facilitate businesses to devise a plan to prevent cyber threat and the risk of legal issues, financial losses and company failures – before accepting the residual risk.
Business Continuity
As all businesses revolve and evolve based on their data, information is critical for ensuring business continuity. Since cyber threats and cyber theft do happen, it is important that businesses possess the capabilty to respond well- this includes having a plan in place to respond to the incident swiftly, professionally and with minimal impact.
A business needs to recognise its capability to access the right information to mitigate the effect of a cyber attack. Key questions that any manager, executive or business owner must ask themselves are:
– Does the information governance system, including cybersecurity policies and procedures, mandate backup of information assets, systems and data that can retried if a cyber incident leads to operational downtime?
– Is there proof the business has a written down business continuity plan and are all employees that will need to act on it trained and knowledgeable as to what to do if the risk occurs?
– It is essential that all employees and effected parties have access to information on how to respond to an incident to minimise any damage? And is this process exactly what cyber insurers want to see in place, in order to mitigate their own exposure?
Trust
Trust and relationships are the biggest factor in ensuring long term sustainability of a business. A savvy cyber insurance company will not accept the transfer of risk if a business cannot demonstrate adequate measures for maintaining trust of all stakeholders and most importantly, customers. Businesses are expected to prove their integrity through questions such as:
– In storing customer data, does the business ensure information governance in collection, storage, use and archiving of data. Is the information encrypted or deidentified? Should customer information fall into the wrong hands, can the customer trust that the business can keep their identity safe?
How frequent and proactive is the security management practice of the business? Has the business got access to notification templates for notifying its customers of a data breach?
Cyber incidents affect company reputation and investor relations, which is why it is important that companies build their risk management strategies transparently and with clarity.
People, Policies & Procedures
A cyber insurance company will delve in to the business processes and policies before agreeing to a commitment. They will analyse a number of things, including:
– Are roles and responsibilities understood?
– Does information governance dictate checks for monitoring access rights to the information and misuse of access rights?
– Are their approval controls for transfer of funds?
– Does the business have an adequate privacy policy that communicates to stakeholders how the business collects and manages information?
– Does the business have a regular patch management policy?
– Does the business have a policy of ensuring ownership of risk and liability is described in all third part contracts?
Compliance, Disclosure & Transparency
Compliance is vital to a cyber insurance company – particularly for the legal team. The insurer will look at the below aspects of the potential business:
– What information governance, risk management, security standards does the business conform to?
– Is the business PCI compliant?
– Does the business comply with the Privacy Act?
– Has the business had a data privacy incident in the past?
– When completing the application form, has a Director of the company signed the insurance application form?
Transferring risk to a third-party insurer must be supported by evidence of information governance. Any negligence on information governance practices reflects the inability of a part of the business to take the right actions to prevent and mitigate a cyber incident.
Buying a Policy
Risk Register
While the myths on policy coverage are rampant, insurance policies are not to be blamed. Not only are the the complexities of cyber risk not well understood, executives are unable to dedicate enough resources to demonstrate adequate information governance measures.
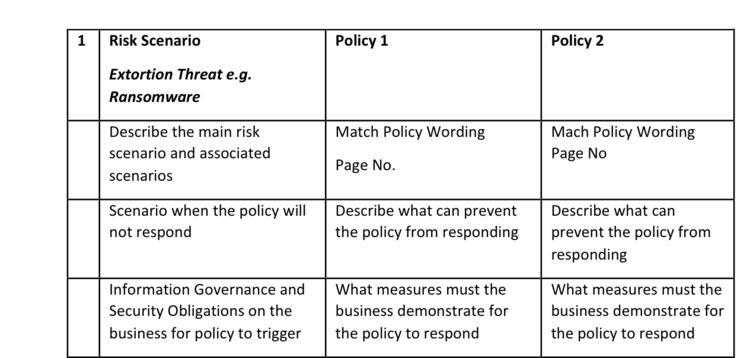
Policy wordings are designed to respond to specific cyber risk scenarios. Businesses seeking to buy a cyber policy must ensure that they articulate cyber scenarios in their risk register and seek insurance for them. Cyber risk scenarios and their potential impact must be eliminated and mitigated and only residual risk must be transferred.
Risk scenarios must be matched with plain policy wording and extent of coverage, for those scenarios must be obvious. Managers who do not carry out this exercise are lacking in the process to invest in insurance.
It is vital that cyber insurance policies suit both the insured and the business needs. This is easy to do with the help of a cyber insurance broker, as they will be able to recommend the most adequate cyber insurance policy and help negotiate the most suitable policies to match the business needs.
Role of Insurance Broker
Cyber risks are evolving. With technology becoming more advanced each day, it is difficult for companies to keep up. With emergent risks, traditional brokers have found it hard to move up the learning curve. Specialist cyber insurance brokers are able to discuss and analyse the business needs, requirements and obligations. They also understand complexities of cyber risk. A broker can help a business to understand coverage, limits, exclusions and deductibles. At the time of buying cyber insurance, a cyber insurance broker will advise a business on how to obtain a health check on all insurance policies so that gaps in total coverage are not taken for granted. A broker will also alert clients on their ongoing obligations for all cyber risk scenarios for which policy wordings are sought and matched.
Businesses wishing to assess their cyber risk can source a quote from a broker and know the cost of their cyber risk. Seeking a quote is free of charge and obligation.
Seeking a Cyber Insurance Quote
Usually your broker can procure an indication quote based on the questions below. However, a final quote can only be based on information provided in the full application form.
1. What was your revenue in last 12 months? Yes/No
2. What policy limit do you require? Yes/No
3. What industry is your business in? Yes/No
4. How many records does your business hold? Yes/No
5. Do you have a business continuity plan? Yes/No
6. Do you encrypt data held by your company on mobile and other devices? Yes/No
7. Do you have firewalls, malware detection systems in place? Yes/No
8. Do you store data on a third party cloud? Who is the cloud service provider? Yes/No
9. Do your contracts indemnify any third party for a data breach? Yes/No
10. Has your business had a data breach in the last two years? Yes/No
11. Do you regularly implement a written patch management process? Yes/No
12. Do you have a privacy policy? Yes/No
13. Which state is your business located?
Cyber insurance policies come equipped with a panel of experts who are able to identify risks and reduce the impact of an incident response. They also have a skilled PR team, legal experts to minimise any associated threats or breach costs, and forensic experts that are able to decipher exactly what happened, why it happened and how to best avoid future incidents from occurring.
Disclaimer: “The information provided is general advice only and does not take account of your personal circumstances or needs. Please refer to our financial services guide which contains details of our services and how we are remunerated.”

